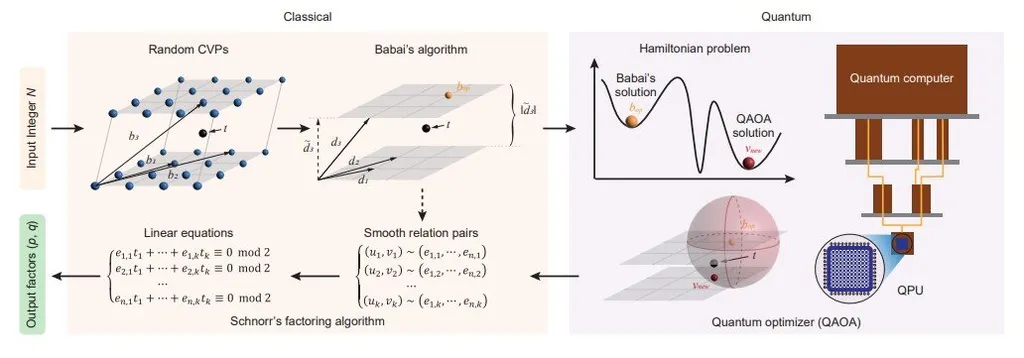
In a groundbreaking development that could reshape the landscape of cryptography and digital security, researchers have successfully simulated Shor’s algorithm to solve discrete logarithm problems (DLP) for a comprehensive range of modulo and order pairs. This work, led by Kaito Kishi from the Quantum Laboratory at Fujitsu Research in Kawasaki, Japan, and published in the IEEE Transactions on Quantum Engineering (translated as the “Journal of Quantum Engineering”), provides critical insights into the practical implications of quantum computing on classical cryptographic systems, with significant ramifications for the energy sector and beyond.
The discrete logarithm problem, a cornerstone of classical cryptography, has long been considered secure against polynomial-time solutions on classical computers. However, Shor’s algorithm, which runs on quantum computers, threatens to upend this paradigm. Kishi and his team constructed quantum circuits to solve DLPs for all 1,860 possible pairs of modulo \( p \) and order \( q \) up to 32 qubits, using a quantum simulator with PRIMEHPC FX700. This extensive simulation has clarified the detailed waveform shape of the success probability of Shor’s algorithm, a periodic function of order \( q \).
“Our work provides a comprehensive analysis of Shor’s algorithm’s success probabilities, which had previously been heuristically analyzed,” Kishi explained. “By simulating these quantum circuits, we were able to verify the theoretical predictions and gain a deeper understanding of the algorithm’s behavior.”
The research also generated 1015 quantum circuits for larger pairs of \( p \) and \( q \), extrapolating the circuit sizes obtained and comparing them for \( p = 2048 \) bits between safe-prime groups and Schnorr groups. While classical cryptography considers these groups to have equal cipher strength when \( p \) is equal, the study quantitatively demonstrated the reduced strength of Schnorr groups when subjected to Shor’s algorithm.
“Interestingly, we found that the cryptographic strength of a Schnorr group with \( p = 2048 \) bits under Shor’s algorithm is almost equivalent to that of a safe-prime group with \( p = 1024 \) bits,” Kishi noted. This finding has profound implications for the energy sector, where secure digital signatures and public key cryptography are essential for protecting critical infrastructure and ensuring the integrity of energy transactions.
The energy sector, in particular, relies heavily on robust cryptographic systems to secure communications and transactions. The potential vulnerability of Schnorr groups to quantum attacks underscores the need for the industry to adopt more resilient cryptographic methods. As quantum computing continues to advance, the energy sector must stay ahead of the curve to protect its digital assets and maintain operational security.
This research not only advances our understanding of quantum algorithms but also highlights the urgent need for the development of post-quantum cryptographic standards. As Kishi’s work demonstrates, the transition to quantum-resistant cryptography is not just a theoretical concern but a practical necessity. The energy sector, along with other industries, must prepare for this shift to ensure the security and integrity of their digital infrastructure in the face of emerging quantum threats.
In conclusion, Kishi’s research published in the IEEE Transactions on Quantum Engineering (Journal of Quantum Engineering) marks a significant step forward in the field of quantum cryptography. By providing a detailed analysis of Shor’s algorithm and its implications for classical cryptographic systems, this work offers valuable insights that will shape the future of digital security. As the energy sector and other industries navigate the complexities of quantum computing, the findings of this study will be instrumental in guiding the development of more secure and resilient cryptographic solutions.